The Silent War at the Heart of the Bitcoin Network

How nodes, mempool policies, and alternative implementations became Bitcoin’s new battlefield
Bitcoin’s value has just dropped by 23%. You stare at the screen, trying to convince yourself it’s a glitch. You refresh the page, but the numbers stay the same, red and unforgiving. Then you come across a piece of news that freezes your blood: Coinbase is holding bitcoins on the wrong chain, a minority branch of the blockchain created after a hard fork. The 23% drop applies to the “real” Bitcoin, but not to the one you own. What you believed was your Bitcoin has just become an almost worthless digital shadow. You were planning to retire next week, and now you realize your savings didn’t merely lose part of their value; they have turned into a string of numbers nobody cares about anymore.

This fragment of a fictional story is grounded in a real historical event from 2013, when, in March, the Bitcoin network experienced a serious technical incident. The blockchain temporarily split into two incompatible chains, triggering market panic and a brief but sharp price drop.
The problem arose from a combination of a bug in the data structure used at the time and differences between versions of the Bitcoin Core software. Part of the network began accepting blocks that the rest of the network rejected, resulting in the spontaneous formation of two chains operating under different rules.
A resolution was reached only after developers, node operators, and the largest miners coordinated their response, temporarily halted transactions, and reverted most of the network to an older software version. The chain backed by greater economic support ultimately “won.”
This event permanently raised questions about Bitcoin’s resilience to software errors and highlighted the need for multiple, independent implementations.
How a Bitcoin Transaction Actually Comes to Life
Behind every Bitcoin transaction, a small technical drama unfolds in three acts. The first begins the moment you press “send.” The transaction does not go straight into the blockchain; instead, it enters the mempool, a kind of digital waiting room of the Bitcoin network. There it remains alongside thousands of others, while computers scattered across the globe receive it, verify it, and relay it further.
The second act is taken over by miners. From the mempool, they select transactions, assemble them into blocks, and expend computational power to find the cryptographic solution that “locks” a new block into the chain.
The third act arrives only once the block is accepted: the transaction moves from promise to fact, from the mempool into the blockchain.
Yet this drama does not unfold on the miners’ stage, but on the infrastructure formed by nodes. Today, around twenty-five thousand independent computers make up the backbone of the Bitcoin network. They receive transactions, maintain the mempool, verify blocks, and store their own copy of the blockchain, without trusting anyone else.
In other words, the principal actors of the Bitcoin network are nodes and miners. While miners are rewarded for their work with newly minted bitcoins and transaction fees, node operators appear to gain no direct financial benefit. Yet without them, there is no stage, no rules, and no audience. Their role is fundamental.

Privacy, Validation, and the Mechanism of Control
Any Bitcoin holder who wants to maintain a high level of privacy can conduct transactions truly securely only if they trust the node they are communicating with. When using a personal node and routing traffic through the Tor network, the sender’s network identity is effectively concealed, allowing the transaction to enter the network without revealing the real IP address.
But privacy is only one side of the story. Nodes independently verify every block and every transaction: signatures, amounts, miner rewards, and all consensus rules. If a miner attempts to push an invalid block, nodes simply reject it, without debate and without voting.
This is precisely why nodes are not passive observers of the network, but its mechanism of control. Bitcoin’s rules do not live in documents or developer statements; they live in thousands of software instances that enforce them every day. The more numerous and the more diverse these instances are, the more resilient Bitcoin becomes to censorship, external pressure, and attempts to reshape the rules from the outside.
And it is exactly at this level, far removed from exchanges, prices, and headlines, that the most important change in the Bitcoin network is taking place today.
Knots — A Tool, Not an Ideology
If we look at what is happening today with Bitcoin and the software that runs its nodes, one trend becomes increasingly clear: the number of operators using alternative implementations is growing rapidly. In absolute terms, their share remains relatively modest, at around 20%, but the pace of change is striking. The number of nodes running alternatives to Bitcoin Core rose from roughly 250 in the summer of 2024 to approximately 5,400 by February 2025, according to data from services such as coin.dance and Bitnodes.
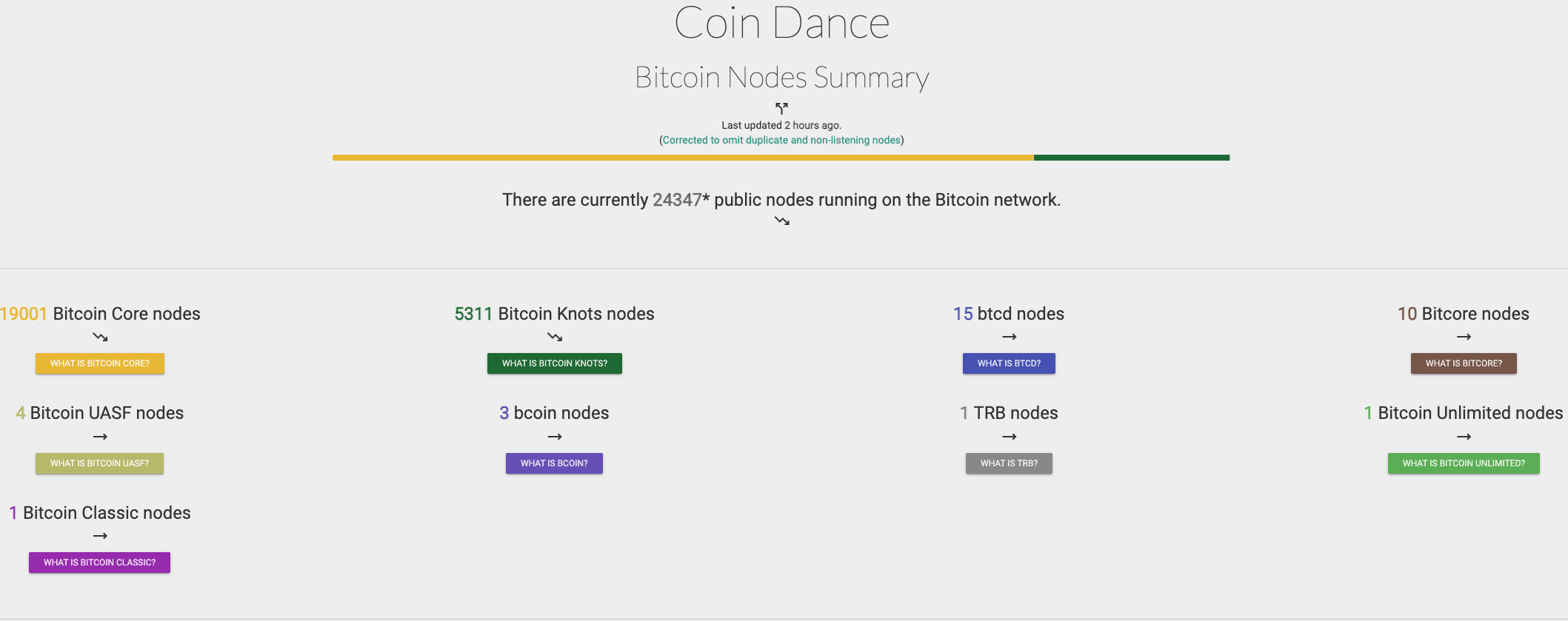
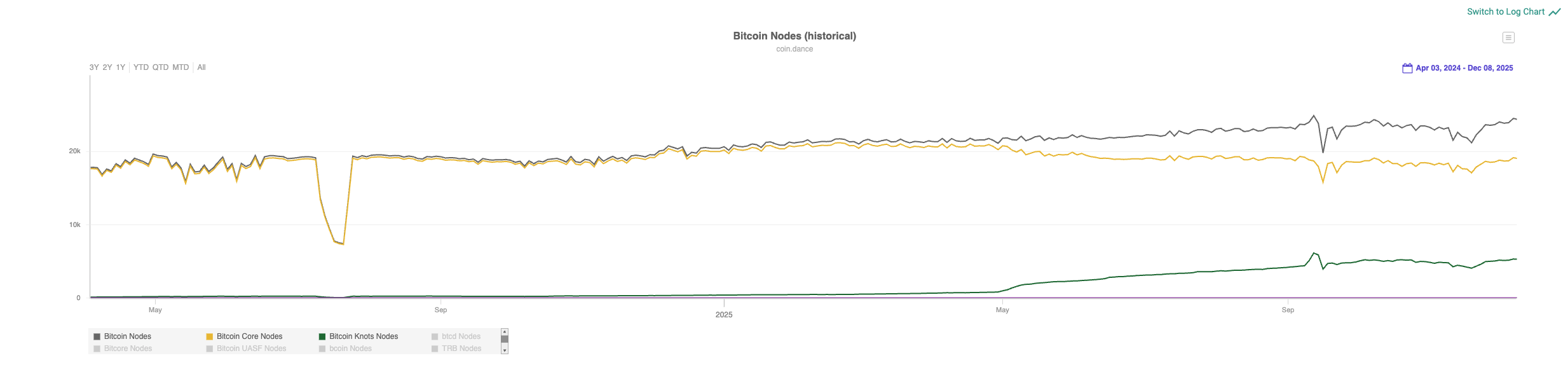
At the center of this growth is Knots which is a Bitcoin node implementation compatible with Bitcoin Core, but with different defaults and transaction relay policies. Knots is not gaining traction because it is “better” in the conventional sense, but because decisions made within Bitcoin Core, particularly around mempool policies and transaction relay rules, are increasingly perceived as overly centralized and too permissive toward behavior resembling spam.
Although it remains technically compatible with Core, Knots offers node operators a much broader set of tools: from more aggressive transaction filtering and finer-grained control over the mempool, to greater influence over which types of data a node is willing to relay across the network.
What Is “Spam” in Bitcoin — and Why It Has Become a Flashpoint
In the Bitcoin ecosystem, “spam” is typically understood to mean transactions that have no genuine economic purpose, but instead primarily serve to occupy block space, burden the network, or push alternative uses of Bitcoin.
This category often includes Ordinals and inscriptions, BRC-20 and similar tokens, artificially generated transaction waves, as well as so-called dust transactions. Some see all of this as a legitimate expression of a free market, while others view it as a degradation of Bitcoin’s monetary function. It is precisely along this fault line that both the ideological and technical conflict emerges.
Ordinals and inscriptions, however, are not an abstract concept. They refer to a mechanism that assigns identity to individual satoshis and enables the permanent inscription of images, text, or other content directly into the witness portion of Bitcoin transactions. In this way, NFT-like records are created on Bitcoin, without smart contracts, but with very real consequences: increased pressure on the mempool, rising transaction fees, and a lasting change in the structure of data being written to the blockchain.
Consensus Without Schism — but Not Without Struggle
Will all of this lead to a new hard fork? Most likely not. Bitcoin’s incentive structure naturally gravitates toward consensus, and history shows that the network strongly avoids permanent splits. Yet the rise of alternative implementations such as Knots carries a deeper, longer-term message: the more independent software, differing policies, and genuine node-level autonomy exist, the harder it becomes for any single team, ideology, or interest group to quietly steer Bitcoin in a direction that does not reflect the will of the broader network.
Because in the end, Bitcoin is not secured by exchanges, developers, or miners. It is secured by thousands of other people’s computers, run for their own reasons, under their own rules, and with their own understanding of what Bitcoin is, and what it must never become. And as long as that remains true, the scenario from the beginning of this story stays exactly that: fiction. But also a reminder of how thin the line is between stable consensus and the wrong branch of history.
This article is part of Crypto Unlocked, a long-term personal hub for understanding blockchain infrastructure, DeFi protocols, and the mechanics of digital money.
© 2026 TC All rights reserved.
This article is protected by copyright law. Any reproduction, distribution, publication, adaptation, storage, or use of this content, in whole or in part, in any form, without the prior written permission of the author is strictly prohibited.
For permissions or licensing inquiries: agemost@protonmail.com

